In an age where data breaches and cyber threats are increasingly sophisticated, traditional security models are no longer sufficient. Zero-trust architectures (ZTA) have emerged as a revolutionary approach, fundamentally reshaping how organizations secure data pipelines and workflows. Unlike legacy systems that rely on perimeter defenses, ZTA assumes that every entity—whether inside or outside the network—is a potential threat. This post explores the transformative role of zero-trust architectures in data engineering and how they pave the way for secure decentralized workflows.
Understanding Zero-Trust in Data Engineering
What is Zero-Trust Architecture?
Zero-trust is a security framework that eliminates implicit trust, enforcing strict verification for every user, device, and data request. This model replaces outdated perimeter-based defenses with a dynamic system where all interactions with data pipelines are authenticated, authorized, and continuously monitored. In the context of data engineering, ZTA ensures that data flow remains secure across hybrid environments, whether it’s cloud-native, on-premises, or edge computing systems. By adopting this model, organizations can proactively address security challenges in decentralized workflows that span geographies and involve multiple stakeholders.
Key Principles of Zero-Trust
- Never Trust, Always Verify: Assume breach and continuously authenticate users and systems.
- Least Privilege Access: Grant minimal access required to perform specific tasks.
- Micro-Segmentation: Divide networks into smaller zones to contain breaches.
- Continuous Monitoring: Use advanced analytics to detect and mitigate anomalies in real time.
Challenges in Securing Decentralized Workflows
The Complexity of Distributed Systems
Decentralized workflows often span multiple cloud providers, on-premises data centers, and edge devices, introducing layers of complexity in enforcing consistent security policies. Each environment operates with distinct configurations and potential vulnerabilities, making it crucial for zero-trust architectures to integrate seamlessly. The key challenge lies in managing a cohesive security framework that adapts to these varying conditions while maintaining real-time visibility across all systems.
Managing Data Privacy
With decentralized workflows, sensitive data becomes more vulnerable as it traverses diverse systems. Unauthorized access, API vulnerabilities, and unencrypted transfers are significant risks in such environments. Implementing zero-trust policies mitigates these threats through robust end-to-end encryption, secure API gateways, and meticulously crafted access controls that operate on the principle of least privilege. These measures ensure that sensitive information remains protected at every stage of the data lifecycle.
Operational Overheads
Zero-trust requires substantial investments in infrastructure, automation, and cybersecurity expertise. Organizations must allocate resources to implement identity management systems, AI-driven monitoring tools, and encrypted communication protocols. Despite these upfront costs, the long-term benefits are undeniable. By drastically reducing the risk of catastrophic breaches and ensuring compliance with stringent data regulations, zero-trust frameworks ultimately safeguard both financial and reputational assets.
Transformative Strategies for Zero-Trust Data Engineering
1. Identity-Centric Security
Implement identity as the new perimeter to redefine access control. Every user and device must authenticate through multi-factor authentication (MFA) mechanisms and identity providers (IdPs) that verify their credentials dynamically. This approach ensures that only legitimate entities gain access, and every request is scrutinized in real-time to prevent unauthorized entry.
2. Secure API Gateways
Zero-trust systems rely on secure APIs to mediate data exchanges. Use API gateways with built-in authentication, throttling, and anomaly detection.
3. Immutable Data Pipelines
Leverage technologies like blockchain to create immutable audit trails. These ensure data integrity and provide tamper-proof evidence for compliance.
4. Real-Time Threat Intelligence
Incorporate AI and machine learning to monitor data flows and detect anomalies. Real-time analytics can identify threats before they escalate.
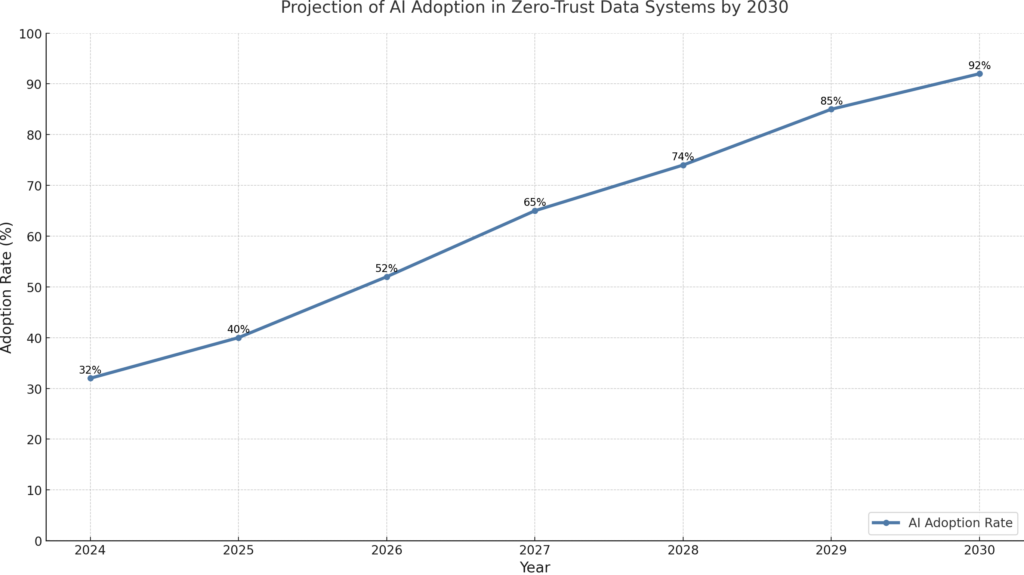
Benefits of Zero-Trust Architectures in Data Engineering
Enhanced Security Posture
By eliminating implicit trust, zero-trust architectures drastically reduce the attack surface and improve threat detection capabilities.
Regulatory Compliance
ZTA helps organizations adhere to global data regulations like GDPR and HIPAA by ensuring data access is tightly controlled and auditable.
Improved Resilience
Micro-segmentation and continuous monitoring make data systems more resilient to breaches, ensuring business continuity even during attacks.

The Future of Zero-Trust in Data Engineering
Integration with Quantum Security
As quantum computing emerges, zero-trust systems must evolve to incorporate quantum-resistant algorithms and encryption methods.
Autonomous Security Frameworks
AI-driven zero-trust systems will autonomously enforce policies, detect threats, and adapt to evolving risks in decentralized workflows.
Greater Adoption of Blockchain
Blockchain will play a pivotal role in creating immutable records and ensuring data integrity in zero-trust environments.
Conclusion
Zero-trust architectures represent a paradigm shift in securing data engineering workflows. By prioritizing verification, limiting access, and embracing continuous monitoring, organizations can fortify their decentralized systems against evolving cyber threats. As data engineering continues to evolve, zero-trust will remain at the forefront, enabling secure and resilient workflows for the digital age.
Key takeaway: Embracing zero-trust is no longer optional; it is an essential strategy for safeguarding decentralized data engineering workflows in an increasingly complex threat landscape..